Is Cloud Computing Safe for Your Business?

As the cloud buzz is getting louder with every passing day you are tempted to take the big leap into the cloud but may have restrained yourself paranoid by ad infinitum cloud security discussions floating on the web. No one can deny the fact that your data is the lifeblood your business. So, undoubtedly its security is of paramount importance for survival of your business. As cloud computing is a paradigm shift from the traditional ways of using computing resources, you must understand its practical security aspects.

Is Cloud Computing Safe?
There can’t be a binary answer (Yes or No) to this question. But with my experience and as an authority on the subject I can tell you that technologies enabling Cloud services are not in any way less secure than the traditional or on-premise hosting model. Also, with the evolution of technology, the cloud providers are getting matured and almost all the providers are offering built-in security, privacy, data backups and risk management as a part of their core service.If you are not a big IT company then you must ask yourself:
· Can an on-premise solution or a traditional hosting provider match the same level of standard security and privacy requirement as provided by the specialist cloud provider whose core competency lies in providing state of the art security and privacy?
· Even if you try to set up something on your own, to match their standard and scale, would it be cost effective in terms of time and skill requirement?
If both your answers to above questions are in negative then Cloud is the best move you can make to acquire a competitive edge over your business rivals.
Yes, it’s always better that you focus on your core business and innovate there and let the specialists do their job for you. They have gained this expertise over a period of time and after investing considerable amount of time and money in innovation.
What do you must Understand Before Signing up a Cloud Provider?
1. What are the Cloud Service Models?(As identified by NIST, National Institute of Standards and Technology, U.S. Department of Commerce)
· SaaS (Software as a Service)
This is a hassle free pay as you use (subscription based) software service model where you don’t need to worry about any other aspect of the service. You just need a browser to access the service. A real world analogy could be the electricity service. You pay for what you use and don’t worry about the underlying power lines, power plant and grid etc.
o Target users: Anyone can use SaaS – Layman, SMBs and Enterprises.
o Example: Dropbox, Google Apps, Microsoft Office 365 etc. There are free SaaS as well like Gmail.
· PaaS (Platform as a Service)
Practically, this service provides a platform for software development, testing and deployment.
o Target users: Developers, Testers and Deployment teams.
o Example: Windows Azure, Google Apps Engine.
· IaaS (Infrastructure as a Service)
This service is the foundation for PaaS and SaaS. Infrastructure components like computers, network, virtual machines, routers and hypervisor etc. forms IaaS.
o Target users: SaaS and many PaaS providers are clients of IaaS.
o Example: Amazon EC2, Rackspace cloud servers.
2. What are the Cloud Deployment Models?
· Private cloud
· Community cloud
· Public cloud
· Hybrid cloud
Due to the simplicity and ease of use, most of the organizations (specifically the SMBs, Small and Medium Businesses) and general consumers opt for SaaS on a Public Cloud. Dropbox is a good example of this. Unlike SaaS, the IaaS and PaaS requires IT teams with highly specialized skills for consuming these services. For example, most of the SaaS vendors are customers of PaaS or IaaS providers.
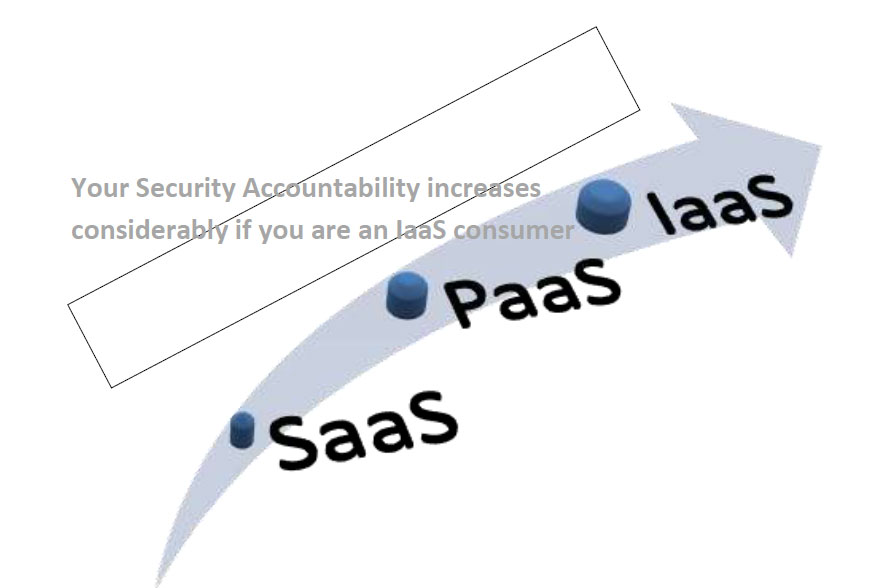
Here you must take a note of something important that could be crucial to your decision making process. Security Accountability of SaaS on Public Cloud lies mostly with the provider whereas IaaS on a Private Cloud will have most of the security responsibility with the customer i.e. you. But at the same time you must understand that IaaS offers you with far more control over the cloud environment and data than SaaS.
· Choosing IaaS or PaaS you’ve more control on your data and computational resources. But here you must understand the security implications i.e. you own the major responsibility to secure your data and environment. Whereas in SaaS most of the security requirements are managed by the service provider.
|
Your Security Accountability increases considerably if you are an IaaS consumer |
3. How are Cloud Data Backup and Replication Executed?
In a cloud environment Backup and Replication are automated processes. These terms are a part of “Disaster Recovery and Business Continuity” process. Every cloud provider has well defined standard DR (Disaster Recovery) practices and they have to follow it religiously as their reputation is at stake in case they fail to live up to their service guarantee.
· Backup: Backups are scheduled and your data is automatically saved at a regular interval. The frequency may depend on the type of data i.e. critical and new data are backed up frequently. So, backup creates versions of data at a different point in time. Backups can be ‘restored’ whenever required.
· Replication: It is storing same set of data on multiple servers with in a data center or multiple data centers spread across different geo-locations. This helps in instant failover support in case of any man-made or natural disaster.
Â?Â?Depending up on the data criticality level, you must have a strong SLA (service level agreement) to ensure a reliable failover support from your provider.
4. Do You Need to Care for Operational Compliance Standards and Certifications of the Cloud Provider?
In brief, YES. Legal requirements may vary from one country to another. As a business owner the sole responsibility of adhering to these compliance requirements lies with you and not with the service provider. So, before you sign-up for any service check for its compliance standards and certifications.
· If you are a
o Healthcare provider in US, you must opt for a cloud service which is HIPAA compliant.
o Payment Processing Provider you must opt for a PCI DSS compliant service.
· For customers in U.S. and European Union (EU) customers, it is always better if the provider is in the U.S.-EU Safe Harbor List.
· EU based companies may need to comply with the additional set of compliance standards, The EU Model Clauses, to address the international transfer of data.So they must select a provider who is ready to sign data processing agreement containing EU model clauses.
· Good if the provider has a few of ISO/IEC 27000-series certifications, specifically ISO/IEC 27001. There are 21 published standards in this series. This series standards are related to the protection of information assets.
ü In brief, the provider you have selected must address your compliance requirements.
5. What are the Contractual Obligations / Service Agreements?
As a standard industry practice most of the providers have predefined non-negotiable agreements which can address general service availability, performance and security concerns. Non-negotiated agreements are a cost effective way of maintaining standard service deliveries based on the economies of scale.
If you have some specific security concerns or compliance standards to follow, sign up a negotiated agreement with your provider. A service with negotiated contracts may be a bit more expensive than a service provided with non-negotiable agreement. For example, EU based customers may require that the provider sign-up an agreement containing EU model clauses.
â?? If you’ve mission critical data go for negotiated contracts.
Questions You Must ask before Signing up a Service
You must double check some specific facts by asking the following set of questions to your provider. The answers provided over here are general industry standard and practices followed by all major providers. Now you have a clue as what to expect as a satisfactory answer.
1. Who owns the data I put in your service?
· You retain the ownership and control of your data.
2. Can I get data out of your service whenever I want?
· Yes. You can extract your data whenever you want in some portable format typically on a self-service basis.
3. Where is my data located?
· It is based on your location. In cases where a company needs to meet the operational compliances related to geo-location of data, it can designate in which physical region its data and server should be located.
4. What is your availability SLA?
· 99.9% uptime in most cases. (At times guaranteed by a financially backed service level agreement).
5. Are you backing up my data?
- Yes. We replicate your data at multiple data centers. This is to ensure reliability and rapid recovery.
6. Privacy standards: Are you in U.S.-EU Safe Harbor List?
· You can check here if the provider is there in the U.S.-EU SAFE HARBOR LIST
What is Your Responsibility After Sign-up?
Your responsibility doesn’t end after exercising due diligence to select the best available cloud provider suitable for your requirement. The real challenge begins once you start using the service. No matter what level of security is provided at the server end by the provider if there are not enough measures to prevent data theft, password breach etc. at client end, your data is bound to be compromised by your own employees, partners and crackers etc.
Provided the cloud service can be accessed easily from any device and from anywhere, makes the task of monitoring very difficult and challenging for you. What if any one of the ubiquitous smart-phones used by your employees to access the cloud service is compromised? Yes, it can lead to critical security issues. Also remember that physical security of client infrastructure and environment is equally important. What if someone walks away with your data in a thumb drive? Let us see the following example:
In context of cloud computing, emails are SaaS mostly on a Public cloud. So, the major part of the security of the service lies solely with service provider. But what’s the use of a bulletproof server side security if a cracker has successfully logged into your email account using your too-easy-to-guess password? Interestingly, in the past, a majority of email breaches occurred because of poor password practices at the client/consumer end. Fortunately, in most of the breaches the data can be restored instantly without any loss. But… it may lead to serious security threats if the cracker gains access to your bank account using your email account.
That's the reason why email providers are now providing an optional “2-Factor-Authentication". This is an extra layer of security using your registered mobile phone. Gmail is the 1st to introduceit. These security measures must be encouraged in any organization.
ü Robust process must be implemented to safeguard your data (at client end) from malicious employees or external threats like crackers.
Bottom-line
Do remember, no matter how best prepared you are, in the online world, things can go wrong and will go wrong. But the beauty of the cloud computing lies in the fact that it preaches Design for Failure. The technologies powering cloud are already matured and reliable. So, the onus of security lies mostly on the one who is going to implement it, i.e. how well the security practices are implemented both at the provider end (i.e. server) and at the consumer end (i.e. client). Go ahead with the cloud as the pros in terms of performance, efficiency and cost far outnumber the cons in terms of security.
other blog entries
Course Directory [training on all levels]
- .NET Classes
- Agile/Scrum Classes
- AI Classes
- Ajax Classes
- Android and iPhone Programming Classes
- Azure Classes
- Blaze Advisor Classes
- C Programming Classes
- C# Programming Classes
- C++ Programming Classes
- Cisco Classes
- Cloud Classes
- CompTIA Classes
- Crystal Reports Classes
- Data Classes
- Design Patterns Classes
- DevOps Classes
- Foundations of Web Design & Web Authoring Classes
- Git, Jira, Wicket, Gradle, Tableau Classes
- IBM Classes
- Java Programming Classes
- JBoss Administration Classes
- JUnit, TDD, CPTC, Web Penetration Classes
- Linux Unix Classes
- Machine Learning Classes
- Microsoft Classes
- Microsoft Development Classes
- Microsoft SQL Server Classes
- Microsoft Team Foundation Server Classes
- Microsoft Windows Server Classes
- Oracle, MySQL, Cassandra, Hadoop Database Classes
- Perl Programming Classes
- Python Programming Classes
- Ruby Programming Classes
- SAS Classes
- Security Classes
- SharePoint Classes
- SOA Classes
- Tcl, Awk, Bash, Shell Classes
- UML Classes
- VMWare Classes
- Web Development Classes
- Web Services Classes
- Weblogic Administration Classes
- XML Classes
did you know? HSG is one of the foremost training companies in the United States
Our courses focus on two areas: the most current and critical object-oriented and component based tools, technologies and languages; and the fundamentals of effective development methodology. Our programs are designed to deliver technology essentials while improving development staff productivity.
An experienced trainer and faculty member will identify the client's individual training requirements, then adapt and tailor the course appropriately. Our custom training solutions reduce time, risk and cost while keeping development teams motivated. The Hartmann Software Group's faculty consists of veteran software engineers, some of whom currently teach at several Colorado Universities. Our faculty's wealth of knowledge combined with their continued real world consulting experience enables us to produce more effective training programs to ensure our clients receive the highest quality and most relevant instruction available. Instruction is available at client locations or at various training facilities located in the metropolitan Denver area.
Upcoming Classes
consulting services we do what we know ... write software
The coaching program integrates our course instruction with hands on software development practices. By employing XP (Extreme Programming) techniques, we teach students as follows:
Configure and integrate the needed development tools
MOntitor each students progress and offer feedback, perspective and alternatives when needed.
Establish an Action plan to yield a set of deliverables in order to guarantee productive learning.
Establish an Commit to a deliverable time line.
Hold each student accountable to a standard that is comparable to that of an engineer/project manager with at least one year's experience in the field.
These coaching cycles typically last 2-4 weeks in duration.
Business Rule isolation and integration for large scale systems using Blaze Advisor
Develop Java, .NET, Perl, Python, TCL and C++ related technologies for Web, Telephony, Transactional i.e. financial and a variety of other considerations.
Windows and Unix/Linux System Administration.
Application Server Administration, in particular, Weblogic, Oracle and JBoss.
Desperate application communication by way of Web Services (SOAP & Restful), RMI, EJBs, Sockets, HTTP, FTP and a number of other protocols.
Graphics Rich application development work i.e. fat clients and/or Web Clients to include graphic design
Performance improvement through code rewrites, code interpreter enhancements, inline and native code compilations and system alterations.
Mentoring of IT and Business Teams for quick and guaranteed expertise transfer.
Architect both small and large software development systems to include: Data Dictionaries, UML Diagrams, Software & Systems Selections and more














