C Programming Training Classes in Brockton, Massachusetts
Learn C Programming in Brockton, Massachusetts and surrounding areas via our hands-on, expert led courses. All of our classes either are offered on an onsite, online or public instructor led basis. Here is a list of our current C Programming related training offerings in Brockton, Massachusetts: C Programming Training
C Programming Training Catalog
Course Directory [training on all levels]
- .NET Classes
- Agile/Scrum Classes
- AI Classes
- Ajax Classes
- Android and iPhone Programming Classes
- Azure Classes
- Blaze Advisor Classes
- C Programming Classes
- C# Programming Classes
- C++ Programming Classes
- Cisco Classes
- Cloud Classes
- CompTIA Classes
- Crystal Reports Classes
- Data Classes
- Design Patterns Classes
- DevOps Classes
- Foundations of Web Design & Web Authoring Classes
- Git, Jira, Wicket, Gradle, Tableau Classes
- IBM Classes
- Java Programming Classes
- JBoss Administration Classes
- JUnit, TDD, CPTC, Web Penetration Classes
- Linux Unix Classes
- Machine Learning Classes
- Microsoft Classes
- Microsoft Development Classes
- Microsoft SQL Server Classes
- Microsoft Team Foundation Server Classes
- Microsoft Windows Server Classes
- Oracle, MySQL, Cassandra, Hadoop Database Classes
- Perl Programming Classes
- Python Programming Classes
- Ruby Programming Classes
- SAS Classes
- Security Classes
- SharePoint Classes
- SOA Classes
- Tcl, Awk, Bash, Shell Classes
- UML Classes
- VMWare Classes
- Web Development Classes
- Web Services Classes
- Weblogic Administration Classes
- XML Classes
- AWS Certified Machine Learning: Specialty (MLS-C01)
20 July, 2026 - 24 July, 2026 - Linux Fundamentals
23 March, 2026 - 27 March, 2026 - RED HAT ENTERPRISE LINUX SYSTEMS ADMIN II
29 June, 2026 - 2 July, 2026 - ASP.NET Core MVC, Rev. 8.0
15 June, 2026 - 16 June, 2026 - ANSIBLE
27 April, 2026 - 29 April, 2026 - See our complete public course listing
Blog Entries publications that: entertain, make you think, offer insight
 The short answer is, yes and no. It depends upon who you are. The purpose of this entry is to help you determine, yes or no.
The short answer is, yes and no. It depends upon who you are. The purpose of this entry is to help you determine, yes or no.
Full disclosure. This entry is created on a Mac mini. And doing so on Windows 8 (Release Preview). If you are a developer, in my humble opinion you need to test on all platforms you expect your app to run or you are not much of a developer.
To be successful you need to leave politics in geographical territory known as Washington DC. My definition of that is: 14 mi.² of real estate surrounded by reality.
Only in politics can we afford to take sides. Those of us in IT, especially developers need to do our best to be all things to all people. Certainly this is a technical impossibility. However in our game we can get some points for at least being serviceable if not outstanding.
In recent decades, companies have become remarkably different than what they were in the past. The formal hierarchies through which support staff rose towards management positions are largely extinct. Offices are flat and open-plan collaborations between individuals with varying talent who may not ever physically occupy a corporate workspace. Many employed by companies today work from laptops nomadically instead. No one could complain that IT innovation hasn’t been profitable. It’s an industry that is forecasted to rake in $351 billion in 2018, according to recent statistics from the Consumer Technology Association (CTA). A leadership dilemma for mid-level IT managers in particular, however, has developed. Being in the middle has always been a professional gray area that only the most driven leverage towards successful outcomes for themselves professionally, but mid-level managers in IT need to develop key skills in order to drive the level of growth that the fast paced companies who employ them need.
What is a middle manager’s role exactly?
A typical middle manager in the IT industry is usually someone who has risen up the ranks from a technical related position due to their ability to envision a big picture of what’s required to drive projects forward. A successful middle manager is able to create cohesion across different areas of the company so that projects can be successfully completed. They’re also someone with the focus necessary to track the progress of complex processes and drive them forward at a fast pace as well as ensure that outcomes meet or exceed expectations.
What challenges do middle managers face in being successful in the IT industry today?
While middle managers are responsible for the teams they oversee to reach key milestones in the life cycle of important projects, they struggle to assert their power to influence closure. Navigating the space between higher-ups and atomized work forces is no easy thing, especially now that workforces often consist of freelancers with unprecedented independence.
What are the skills most needed for an IT manager to be effective?
Being educated on a steady basis to handle the constant evolution of tech is absolutely essential if a middle manager expects to thrive professionally in a culture so knowledge oriented that evolves at such a rapid pace. A middle manager who doesn't talk the talk of support roles or understand the nuts and bolts of a project they’re in charge of reaching completion will not be able to catch errors or suggest adequate solutions when needed.
How has the concept of middle management changed?
Middle managers were basically once perceived of as supervisors who motivated and rewarded staff towards meeting goals. They coached. They toggled back and forth between the teams they watched over and upper management in an effort to keep everyone on the same page. It could be said that many got stuck between the lower and upper tier of their companies in doing so. While companies have always had to be result-oriented to be profitable, there’s a much higher expectation for what that means in the IT industry. Future mid-level managers will have to have the same skills as those whose performance they're tracking so they can determine if projects are being executed effectively. They also need to be able to know what new hires that are being on-boarded should know to get up to speed quickly, and that’s just a thumbnail sketch because IT companies are driven forward by skills that are not easy to master and demand constant rejuvenation in the form of education and training. It’s absolutely necessary for those responsible for teams that bring products and services to market to have similar skills in order to truly determine if they’re being deployed well. There’s a growing call for mid-level managers to receive more comprehensive leadership training as well, however. There’s a perception that upper and lower level managers have traditionally been given more attention than managers in the middle. Some say that better prepped middle managers make more valuable successors to higher management roles. That would be a great happy ending, but a growing number of companies in India’s tech sector complain that mid-level managers have lost their relevance in the scheme of the brave new world of IT and may soon be obsolete.
Facebook was originally intended as a way for people to stay in touch with friends and family members by sharing pictures and status updates on their timeline. As the website's popularity has grown, so has criticism that it is becoming one giant, online high school.
Online Bullying
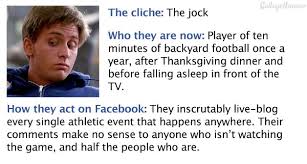 There has been a dramatic increase in recent years in the number of online bullying cases due to the introduction of social media. Bullying isn't just limited to younger Facebook users, either. Many adult users have also resorted to bashing others online through nasty status updates and cruel comments.
There has been a dramatic increase in recent years in the number of online bullying cases due to the introduction of social media. Bullying isn't just limited to younger Facebook users, either. Many adult users have also resorted to bashing others online through nasty status updates and cruel comments.
Prior to social media, bullying in high school involved "kick me" signs and toilet swirling. Facebook and other social media outlets have allowed users to take bullying to a whole other level. Victims can no longer escape bullying by leaving school or work. The torture continues online, at anytime and anyplace.
Status "Likes"
In high school, everyone wants to be part of the popular crowd; people who are outgoing, beautiful, and seem like they have everything. Posting a status update is similar to wanting to be popular. Once an update is posted, many users wait with bated breath to see how many friends will "like" their status. They believe that the more "likes" they receive, the more popular they are.
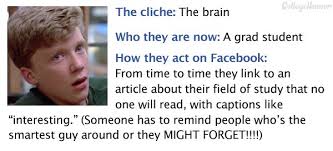 If that isn’t enough, there are many Facebook games that involve "liking" someone's status. Games like "Truth Is", where someone likes a status update and in return the poster writes how they really feel about the friend on their Facebook wall. This can get touchy, especially if the two people aren't friends outside of Facebook. It's similar to high school where someone desperately wants another person to like them, but when they find out how that person really feels they are crushed.
If that isn’t enough, there are many Facebook games that involve "liking" someone's status. Games like "Truth Is", where someone likes a status update and in return the poster writes how they really feel about the friend on their Facebook wall. This can get touchy, especially if the two people aren't friends outside of Facebook. It's similar to high school where someone desperately wants another person to like them, but when they find out how that person really feels they are crushed.
Relationships Are Difficult to Keep Private
When someone signs up for Facebook they’re asked to complete their profile, which includes a relationship section. Users can select from different options including "single", "married", "widowed", and "divorced". Whenever someone changes their relationship status, the update shows up on each of their friend's news feeds.
It's easy to see how this feature correlates with high school where everyone talks about who is dating who or which couple broke up. It used to be that after graduation, people were able to keep their relationships more to themselves. Not so anymore in the age of social media. Now everyone has the ability to state their opinion on a friend's relationship status, either by "liking" their status change or by commenting on it.
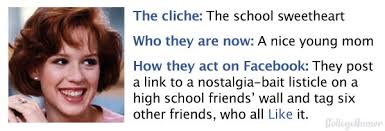 Facebook has presented many benefits to its users, including the ability to rekindle old high school friendships. What one must understand when they sign up for the service is that they are opening themselves up to the same criticism and drama that takes place in a high school setting.
Facebook has presented many benefits to its users, including the ability to rekindle old high school friendships. What one must understand when they sign up for the service is that they are opening themselves up to the same criticism and drama that takes place in a high school setting.
Proceed with caution!
One of the most anticipated features that came on the iPhone 4S was a new thing called: Siri. Zooming out before concentrating on Siri, mobile assistants were the new rage. Beforehand, people were fascinated by the cloud, and how you could store your files in the Internet and retrieve it from anywhere. You could store your file at home, and get it at your workplace to make a presentation. However, next came virtual assistants. When you’re in the car, it’s hard to send text messages. It’s hard to call people. It’s hard to set reminders that just popped into your head onto your phone. Thus, came the virtual assistant: a new way to be able to talk to your phone to be able to do what you want it to do, and in this case, text message, or call people, and many other features. Apple jumped onto the bandwagon with the iPhone 4S and came out with the new feature: Siri, a virtual assistant that is tailored to assist you in your endeavours by your diction.
Getting started with Siri
To get Siri in the first place, you need an iPhone 4S; although you may have the latest updates on your iPhone 4 or earlier, having an iPhone 4S means you have the hardware that is required to run Siri on your phone. Therefore, if you are interested in using Siri, check into getting an iPhone 4S, as they are getting cheaper every single day.
Tech Life in Massachusetts
| Company Name | City | Industry | Secondary Industry |
|---|---|---|---|
| Cabot Corporation | Boston | Telecommunications | Telephone Service Providers and Carriers |
| LPL Financial | Boston | Financial Services | Personal Financial Planning and Private Banking |
| NSTAR Gas and Electric Company | Westwood | Energy and Utilities | Gas and Electric Utilities |
| Cabot Corporation | Boston | Manufacturing | Plastics and Rubber Manufacturing |
| BJ's Wholesale Club, Inc. | Westborough | Retail | Department Stores |
| American Tower Corporation | Boston | Telecommunications | Telecommunications Equipment and Accessories |
| Hologic, Inc. | Bedford | Healthcare, Pharmaceuticals and Biotech | Medical Devices |
| Global Partners LP | Waltham | Retail | Gasoline Stations |
| Northeast Utilities | Boston | Energy and Utilities | Gas and Electric Utilities |
| Liberty Mutual Holding Company | Boston | Financial Services | Insurance and Risk Management |
| Staples Inc. | Framingham | Computers and Electronics | Office Machinery and Equipment |
| Thermo Fisher Scientific Inc. | Waltham | Healthcare, Pharmaceuticals and Biotech | Medical Devices |
| Hanover Insurance Group, Inc. | Worcester | Financial Services | Insurance and Risk Management |
| The TJX Companies, Inc. | Framingham | Retail | Department Stores |
| Iron Mountain, Inc. | Boston | Software and Internet | Data Analytics, Management and Storage |
| Massachusetts Mutual Financial Group | Springfield | Financial Services | Insurance and Risk Management |
| Beacon Roofing Supply, Inc. | Peabody | Manufacturing | Concrete, Glass, and Building Materials |
| Raytheon Company | Waltham | Software and Internet | Software |
| Analog Devices, Inc. | Norwood | Computers and Electronics | Consumer Electronics, Parts and Repair |
| Biogen Idec Inc. | Weston | Healthcare, Pharmaceuticals and Biotech | Biotechnology |
| Boston Scientific Corporation | Natick | Healthcare, Pharmaceuticals and Biotech | Medical Supplies and Equipment |
| PerkinElmer, Inc. | Waltham | Computers and Electronics | Instruments and Controls |
| State Street Corporation | Boston | Financial Services | Trust, Fiduciary, and Custody Activities |
| EMC Corporation | Hopkinton | Computers and Electronics | Networking Equipment and Systems |
training details locations, tags and why hsg
The Hartmann Software Group understands these issues and addresses them and others during any training engagement. Although no IT educational institution can guarantee career or application development success, HSG can get you closer to your goals at a far faster rate than self paced learning and, arguably, than the competition. Here are the reasons why we are so successful at teaching:
- Learn from the experts.
- We have provided software development and other IT related training to many major corporations in Massachusetts since 2002.
- Our educators have years of consulting and training experience; moreover, we require each trainer to have cross-discipline expertise i.e. be Java and .NET experts so that you get a broad understanding of how industry wide experts work and think.
- Discover tips and tricks about C Programming programming
- Get your questions answered by easy to follow, organized C Programming experts
- Get up to speed with vital C Programming programming tools
- Save on travel expenses by learning right from your desk or home office. Enroll in an online instructor led class. Nearly all of our classes are offered in this way.
- Prepare to hit the ground running for a new job or a new position
- See the big picture and have the instructor fill in the gaps
- We teach with sophisticated learning tools and provide excellent supporting course material
- Books and course material are provided in advance
- Get a book of your choice from the HSG Store as a gift from us when you register for a class
- Gain a lot of practical skills in a short amount of time
- We teach what we know…software
- We care…














