Java Programming Training Classes in Pompano Beach, Florida
Training Suggestions from the Experts

An Experienced Java developer must know
... everything or so it can seem. A solid grasp and knowledge of Object Oriented Programming constructs such as inheritance, polymorphism, interfaces and reflection are essential. Next in line is the knowldge to be able to import/export file data, running SQL queries, using regular expressions and, possibly, knowing how to write multi-threaded code and make socket connections. A class that addresses most of these topics is: Fast Track to Java 11 and OO Development.
For the more daring Java enthusiast and especially for those looking to become professional Java developers, knowledge of the Spring Framework is expected. A perfect class for this is: Fast Track to Spring Framework and Spring MVC/Rest. Not only does this course provide students with a great introduction to spring, it goes beyond the basics with a solid delve into Spring and web development.
Another consideration is learning JBoss aka Wildfly, the free Application Server from RedHat. JBoss has become the workhorse of most Java EE applications. Add to that a class on Tomcat, the defacto servlet engine, and the student can be considered 'ready' for employment.
Call for Details: 303.377.6176
Learn Java Programming in Pompano Beach, Florida and surrounding areas via our hands-on, expert led courses. All of our classes either are offered on an onsite, online or public instructor led basis. Here is a list of our current Java Programming related training offerings in Pompano Beach, Florida: Java Programming Training
Java Programming Training Catalog
subcategories
JBoss Administration Classes
JUnit, TDD, CPTC, Web Penetration Classes
Java Enterprise Edition Classes
Java Programming Classes
Spring Classes
Course Directory [training on all levels]
- .NET Classes
- Agile/Scrum Classes
- AI Classes
- Ajax Classes
- Android and iPhone Programming Classes
- Azure Classes
- Blaze Advisor Classes
- C Programming Classes
- C# Programming Classes
- C++ Programming Classes
- Cisco Classes
- Cloud Classes
- CompTIA Classes
- Crystal Reports Classes
- Data Classes
- Design Patterns Classes
- DevOps Classes
- Foundations of Web Design & Web Authoring Classes
- Git, Jira, Wicket, Gradle, Tableau Classes
- IBM Classes
- Java Programming Classes
- JBoss Administration Classes
- JUnit, TDD, CPTC, Web Penetration Classes
- Linux Unix Classes
- Machine Learning Classes
- Microsoft Classes
- Microsoft Development Classes
- Microsoft SQL Server Classes
- Microsoft Team Foundation Server Classes
- Microsoft Windows Server Classes
- Oracle, MySQL, Cassandra, Hadoop Database Classes
- Perl Programming Classes
- Python Programming Classes
- Ruby Programming Classes
- SAS Classes
- Security Classes
- SharePoint Classes
- SOA Classes
- Tcl, Awk, Bash, Shell Classes
- UML Classes
- VMWare Classes
- Web Development Classes
- Web Services Classes
- Weblogic Administration Classes
- XML Classes
- Linux Fundamentals
23 March, 2026 - 27 March, 2026 - AWS Certified Machine Learning: Specialty (MLS-C01)
2 March, 2026 - 6 March, 2026 - Linux Troubleshooting
2 March, 2026 - 6 March, 2026 - ANSIBLE
18 February, 2026 - 20 February, 2026 - RED HAT ENTERPRISE LINUX SYSTEMS ADMIN I
26 January, 2026 - 30 January, 2026 - See our complete public course listing
Blog Entries publications that: entertain, make you think, offer insight

Jeff Nelson, a former Googler and inventor of Chromebook says on Quora, “One habit I've clung to is writing small prototypes when I'm trying to learn new concepts.
For example, I'll sit down with a book or a web page, and over the course of a few hours, write 30 or 40 programs all of them only a few dozen lines long. Each program intended to demonstrate some simple concept. This prototyping makes it very easy to try out many concepts in a short period of time.”
Miguel Paraz, Software Engineering Student habit is to “keep a log in a text file or document on my work computer. Before trying to solve a problem, I write it down first. And then I describe the details as they happen.”
 In most business circles, the question of whether or not a website truly helps a company's business has become somewhat moot. Simply put, a website is a necessary evil, like it or not. The question is no longer, should a company have a website, but rather, is the website optimized to ensure the best potential results. Of course, it is important to understand what is meant by "helping a company."
In most business circles, the question of whether or not a website truly helps a company's business has become somewhat moot. Simply put, a website is a necessary evil, like it or not. The question is no longer, should a company have a website, but rather, is the website optimized to ensure the best potential results. Of course, it is important to understand what is meant by "helping a company."
Many businesses are under the assumption that a website is going to turn into cold hard cash for the company. Well, that could be the case if the organization is using a type of e-commerce platform to buy and sell goods. Many businesses are service oriented and as such, the website serves an entirely different purpose.
Facebook was originally intended as a way for people to stay in touch with friends and family members by sharing pictures and status updates on their timeline. As the website's popularity has grown, so has criticism that it is becoming one giant, online high school.
Online Bullying
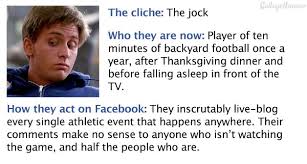 There has been a dramatic increase in recent years in the number of online bullying cases due to the introduction of social media. Bullying isn't just limited to younger Facebook users, either. Many adult users have also resorted to bashing others online through nasty status updates and cruel comments.
There has been a dramatic increase in recent years in the number of online bullying cases due to the introduction of social media. Bullying isn't just limited to younger Facebook users, either. Many adult users have also resorted to bashing others online through nasty status updates and cruel comments.
Prior to social media, bullying in high school involved "kick me" signs and toilet swirling. Facebook and other social media outlets have allowed users to take bullying to a whole other level. Victims can no longer escape bullying by leaving school or work. The torture continues online, at anytime and anyplace.
Status "Likes"
In high school, everyone wants to be part of the popular crowd; people who are outgoing, beautiful, and seem like they have everything. Posting a status update is similar to wanting to be popular. Once an update is posted, many users wait with bated breath to see how many friends will "like" their status. They believe that the more "likes" they receive, the more popular they are.
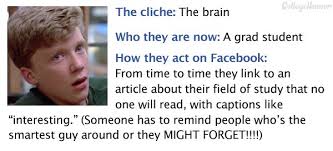 If that isn’t enough, there are many Facebook games that involve "liking" someone's status. Games like "Truth Is", where someone likes a status update and in return the poster writes how they really feel about the friend on their Facebook wall. This can get touchy, especially if the two people aren't friends outside of Facebook. It's similar to high school where someone desperately wants another person to like them, but when they find out how that person really feels they are crushed.
If that isn’t enough, there are many Facebook games that involve "liking" someone's status. Games like "Truth Is", where someone likes a status update and in return the poster writes how they really feel about the friend on their Facebook wall. This can get touchy, especially if the two people aren't friends outside of Facebook. It's similar to high school where someone desperately wants another person to like them, but when they find out how that person really feels they are crushed.
Relationships Are Difficult to Keep Private
When someone signs up for Facebook they’re asked to complete their profile, which includes a relationship section. Users can select from different options including "single", "married", "widowed", and "divorced". Whenever someone changes their relationship status, the update shows up on each of their friend's news feeds.
It's easy to see how this feature correlates with high school where everyone talks about who is dating who or which couple broke up. It used to be that after graduation, people were able to keep their relationships more to themselves. Not so anymore in the age of social media. Now everyone has the ability to state their opinion on a friend's relationship status, either by "liking" their status change or by commenting on it.
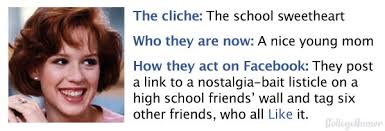 Facebook has presented many benefits to its users, including the ability to rekindle old high school friendships. What one must understand when they sign up for the service is that they are opening themselves up to the same criticism and drama that takes place in a high school setting.
Facebook has presented many benefits to its users, including the ability to rekindle old high school friendships. What one must understand when they sign up for the service is that they are opening themselves up to the same criticism and drama that takes place in a high school setting.
Proceed with caution!
When making a strategic cloud decision, organizations can follow either one of two ideologies: open or closed.
In the past, major software technologies have been widely accepted because an emerging market leader simplified the initial adoption. After a technology comes of age, the industry spawns open alternatives that provide choice and flexibility, and the result is an open alternative that quickly gains traction and most often outstrips the capabilities of its proprietary predecessor.
After an organization invests significantly in a technology, the complexity and effort required steering a given workload onto a new system or platform is, in most cases, significant. Switching outlays, shifting to updated or new software/hardware platforms, and the accompanying risks may lead to the ubiquitousness of large, monolithic and complex ERP systems – reason not being that they offer the best value for an organization, but rather because shifting to anything else is simply – unthinkable.
There’s no denying that these are critical considerations today since a substantial number of organizations are making their first jump into the cloud and making preparations for the upsetting shift in how IT is delivered to both internal and external clientele. Early adopters are aware of the fact that the innovation brought about by open technologies can bring dramatic change, and hence are realizing how crucial it is to be able to chart their own destiny.
Tech Life in Florida
| Company Name | City | Industry | Secondary Industry |
|---|---|---|---|
| Lender Processing Services, Inc. (LPS) | Jacksonville | Software and Internet | Data Analytics, Management and Storage |
| World Fuel Services Corporation | Miami | Energy and Utilities | Gasoline and Oil Refineries |
| SEACOR Holdings Inc. | Fort Lauderdale | Transportation and Storage | Marine and Inland Shipping |
| MasTec, Inc. | Miami | Business Services | Security Services |
| Health Management Associates, Inc. | Naples | Healthcare, Pharmaceuticals and Biotech | Hospitals |
| B/E Aerospace, Inc. | Wellington | Manufacturing | Aerospace and Defense |
| Roper Industries, Inc. | Sarasota | Manufacturing | Manufacturing Other |
| AutoNation | Fort Lauderdale | Retail | Automobile Dealers |
| Watsco, Inc. | Miami | Wholesale and Distribution | Wholesale and Distribution Other |
| SFN Group | Fort Lauderdale | Business Services | HR and Recruiting Services |
| Tupperware Corporation | Orlando | Manufacturing | Plastics and Rubber Manufacturing |
| AirTran Holdings, Inc. | Orlando | Travel, Recreation and Leisure | Passenger Airlines |
| WellCare Health Plans, Inc. | Tampa | Healthcare, Pharmaceuticals and Biotech | Healthcare, Pharmaceuticals, and Biotech Other |
| Lennar Corporation | Miami | Real Estate and Construction | Real Estate Agents and Appraisers |
| HSN, Inc. | Saint Petersburg | Retail | Retail Other |
| Certegy | Saint Petersburg | Business Services | Business Services Other |
| Raymond James Financial, Inc. | Saint Petersburg | Financial Services | Trust, Fiduciary, and Custody Activities |
| Winn-Dixie Stores, Inc. | Jacksonville | Retail | Grocery and Specialty Food Stores |
| Jabil Circuit, Inc. | Saint Petersburg | Computers and Electronics | Semiconductor and Microchip Manufacturing |
| CSX Corporation | Jacksonville | Transportation and Storage | Freight Hauling (Rail and Truck) |
| Fidelity National Financial, Inc. | Jacksonville | Financial Services | Insurance and Risk Management |
| Tech Data Corporation | Clearwater | Consumer Services | Automotive Repair & Maintenance |
| TECO Energy, Inc. | Tampa | Manufacturing | Chemicals and Petrochemicals |
| Lincare Holdings Inc | Clearwater | Healthcare, Pharmaceuticals and Biotech | Medical Supplies and Equipment |
| Chico's FAS Inc. | Fort Myers | Retail | Clothing and Shoes Stores |
| Burger King Corporation LLC | Miami | Retail | Restaurants and Bars |
| Publix Super Markets, Inc. | Lakeland | Retail | Grocery and Specialty Food Stores |
| Florida Power and Light Company | Juno Beach | Energy and Utilities | Gas and Electric Utilities |
| Ryder System, Inc. | Miami | Transportation and Storage | Freight Hauling (Rail and Truck) |
| Citrix Systems, Inc. | Fort Lauderdale | Software and Internet | Software and Internet Other |
| Harris Corporation | Melbourne | Telecommunications | Wireless and Mobile |
| Office Depot, Inc. | Boca Raton | Computers and Electronics | Audio, Video and Photography |
| Landstar System, Inc. | Jacksonville | Transportation and Storage | Freight Hauling (Rail and Truck) |
| Darden Restaurants, Inc. | Orlando | Retail | Restaurants and Bars |
| PSS World Medical, Inc. | Jacksonville | Healthcare, Pharmaceuticals and Biotech | Medical Supplies and Equipment |
training details locations, tags and why hsg
The Hartmann Software Group understands these issues and addresses them and others during any training engagement. Although no IT educational institution can guarantee career or application development success, HSG can get you closer to your goals at a far faster rate than self paced learning and, arguably, than the competition. Here are the reasons why we are so successful at teaching:
- Learn from the experts.
- We have provided software development and other IT related training to many major corporations in Florida since 2002.
- Our educators have years of consulting and training experience; moreover, we require each trainer to have cross-discipline expertise i.e. be Java and .NET experts so that you get a broad understanding of how industry wide experts work and think.
- Discover tips and tricks about Java Programming programming
- Get your questions answered by easy to follow, organized Java Programming experts
- Get up to speed with vital Java Programming programming tools
- Save on travel expenses by learning right from your desk or home office. Enroll in an online instructor led class. Nearly all of our classes are offered in this way.
- Prepare to hit the ground running for a new job or a new position
- See the big picture and have the instructor fill in the gaps
- We teach with sophisticated learning tools and provide excellent supporting course material
- Books and course material are provided in advance
- Get a book of your choice from the HSG Store as a gift from us when you register for a class
- Gain a lot of practical skills in a short amount of time
- We teach what we know…software
- We care…














