Business Analysis Training Classes in Eau Claire, Wisconsin
Learn Business Analysis in Eau Claire, Wisconsin and surrounding areas via our hands-on, expert led courses. All of our classes either are offered on an onsite, online or public instructor led basis. Here is a list of our current Business Analysis related training offerings in Eau Claire, Wisconsin: Business Analysis Training
Business Analysis Training Catalog
Course Directory [training on all levels]
- .NET Classes
- Agile/Scrum Classes
- AI Classes
- Ajax Classes
- Android and iPhone Programming Classes
- Azure Classes
- Blaze Advisor Classes
- C Programming Classes
- C# Programming Classes
- C++ Programming Classes
- Cisco Classes
- Cloud Classes
- CompTIA Classes
- Crystal Reports Classes
- Data Classes
- Design Patterns Classes
- DevOps Classes
- Foundations of Web Design & Web Authoring Classes
- Git, Jira, Wicket, Gradle, Tableau Classes
- IBM Classes
- Java Programming Classes
- JBoss Administration Classes
- JUnit, TDD, CPTC, Web Penetration Classes
- Linux Unix Classes
- Machine Learning Classes
- Microsoft Classes
- Microsoft Development Classes
- Microsoft SQL Server Classes
- Microsoft Team Foundation Server Classes
- Microsoft Windows Server Classes
- Oracle, MySQL, Cassandra, Hadoop Database Classes
- Perl Programming Classes
- Python Programming Classes
- Ruby Programming Classes
- SAS Classes
- Security Classes
- SharePoint Classes
- SOA Classes
- Tcl, Awk, Bash, Shell Classes
- UML Classes
- VMWare Classes
- Web Development Classes
- Web Services Classes
- Weblogic Administration Classes
- XML Classes
- AWS Certified Machine Learning: Specialty (MLS-C01)
20 July, 2026 - 24 July, 2026 - ASP.NET Core MVC, Rev. 8.0
15 June, 2026 - 16 June, 2026 - Linux Fundamentals
23 March, 2026 - 27 March, 2026 - Docker
27 May, 2026 - 29 May, 2026 - RED HAT ENTERPRISE LINUX SYSTEMS ADMIN II
29 June, 2026 - 2 July, 2026 - See our complete public course listing
Blog Entries publications that: entertain, make you think, offer insight
Although reports made in May 2010 indicate that Android had outsold Apple iPhones, more recent and current reports of the 2nd quarter of 2011 made by National Purchase Diary (NPD) on Mobile Phone Track service, which listed the top five selling smartphones in the United States for the months of April-June of 2011, indicate that Apple's iPhone 4 and iPhone 3GS outsold other Android phones on the market in the U. S. for the third calendar quarter of 2011. This was true for the previous quarter of the same year; The iPhone 4 held the top spot. The fact that the iPhone 4 claimed top spot does not come as a surprise to the analysts; rather, it is a testament to them of how well the iPhone is revered among consumers. The iPhone 3GS, which came out in 2009 outsold newer Android phones with higher screen resolutions and more processing power. The list of the five top selling smartphones is depicted below:
- Apple iPhone 4
- Apple iPhone 3GS
- HTC EVO 4G
- Motorola Droid 3
- Samsung Intensity II[1]
Apple’s iPhone also outsold Android devices7.8:1 at AT&T’s corporate retail stores in December. A source inside the Apple company told The Mac Observer that those stores sold some 981,000 iPhones between December 1st and December 27th 2011, and that the Apple device accounted for some 66% of all device sales during that period (see the pie figure below) . Android devices, on the other hand, accounted for just 8.5% of sales during the same period.
According to the report, AT&T sold approximately 981,000 iPhones through AT&T corporate stores in the first 27 days of December, 2011 while 126,000 Android devices were sold during the same period. Even the basic flip and slider phones did better than Android, with 128,000 units sold.[2] However, it is important to understand that this is a report for one particular environment at a particular period in time. As the first iPhone carrier in the world, AT&T has been the dominant iPhone carrier in the U.S. since day one, and AT&T has consistently claimed that the iPhone is its best selling device.

Chart courtesy of Mac Observer: http://www.macobserver.com/tmo/article/iphone_crushes_android_at_att_corporate_stores_in_december/
A more recent report posted in ismashphone.com, dated January 25 2012, indicated that Apple sold 37 million iPhones in Q4 2011. It appears that the iPhone 4S really helped take Apple’s handset past competing Android phones. According to research firm Kantar Worldpanel ComTech, Apple’s U.S. smartphone marketshare has doubled to 44.9 percent.[3] Meanwhile, Android marketshare in the U.S. dropped slightly to 44.8 percent. This report means that the iPhone has edged just a little bit past Android in U.S. marketshare. This is occurred after Apple’s Q1 2012 conference call, which saw themselling 37 million handsets. Meanwhile, it’s reported that marketers of Android devices, such as Motorola Mobility, HTC and Sony Ericsson saw drops this quarter.
Data has always been important to business. While it wasn't long ago that businesses kept minimal information on people who bought their products, nowadays companies keep vast amounts of data. In the late 20th century, marketers began to take demographics seriously. It was hard to keep track of so much information without the help of computers.
Only large companies in the '60s and '70s could afford the research necessary to deliver real marketing insight. The marketers of yesteryear relied upon focus groups and expensive experiments to gauge consumer behavior in a controlled environment. Today even the smallest of companies can have access to a rich array of real-world data about their consumers' behavior and their consumers. The amount of data that is stored today dwarfs the data of only a few years ago by several orders of magnitude.
So what kind of information are businesses storing for marketing purposes? Some examples include:
- Demographic information — age, gender, ethnicity, education, occupation and various other individual characteristics.
Information Technology is one of the most dynamic industries with new technologies surfacing frequently. In such a scenario, it can get intimidating for information technology professionals at all levels to keep abreast of the latest technology innovations worth investing time and resources into.
It can therefore get daunting for entry and mid-level IT professionals to decide which technologies they should potentially be developing skills. However, the biggest challenge comes for senior information technology professionals responsible for driving the IT strategy in their organizations.
It is therefore important to keep abreast of the latest technology trends and get them from reputable sources. Here are some of the ways to keep on top of the latest trends in Information Technology.
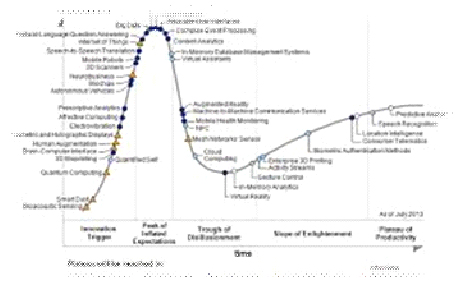
· Subscribe to leading Analyst Firms: If you work for a leading IT organization, chances are that you already have subscription to leading IT analyst firms notably Gartner and Forrester. These two firms are some of the most recognized analyst firms with extensive coverage on almost every enterprise technology including hardware and software. These Analyst firms frequently publish reports on global IT spending and trends that are based on primary research conducted on vendors and global CIOs & CTOs. However, subscription to these reports is very expensive and if you are a part of a small organization you may have issues securing access to these reports. One of the most important pieces of research published by these firms happens to be the Gartner Hype Cycle which plots leading technologies and their maturity curve.Even if you do not have access to Gartner research, you can hack your way by searching for “Gartner Hype Cycle” on Google Images and you will in most cases be able to see the plots similar to the one below
 Attempting to create an intelligent entry about Linux for such a wide ranging audience is a bit like trying to compare a presentation on quantum mechanics for physicists while being readable by somebody with a junior high school education.
Attempting to create an intelligent entry about Linux for such a wide ranging audience is a bit like trying to compare a presentation on quantum mechanics for physicists while being readable by somebody with a junior high school education.
If you are a *NIX expert, then I suggest you keep on reading so you know how to explain this world to mere mortals.
I called it *nix for a reason. It represents a family of thinking. It is not unlike the difference between the language C and C++. Are there differences between the two? Certainly. And it is not like the difference between COBOL and C.
Years ago when I ran my own vo-tech school I would teach the students there are only two things in life. MS and *NIX. A friend of mine, a genius developer in her own right was aghast.
Tech Life in Wisconsin
| Company Name | City | Industry | Secondary Industry |
|---|---|---|---|
| We Energies | Milwaukee | Energy and Utilities | Gas and Electric Utilities |
| Bemis Company, Inc. | Neenah | Manufacturing | Plastics and Rubber Manufacturing |
| Regal Beloit Corporation | Beloit | Manufacturing | Tools, Hardware and Light Machinery |
| Manitowoc Company, Inc | Manitowoc | Manufacturing | Heavy Machinery |
| Briggs and Stratton Corporation | Milwaukee | Manufacturing | Tools, Hardware and Light Machinery |
| Mortgage Guaranty Insurance Corporation (MGIC) | Milwaukee | Financial Services | Lending and Mortgage |
| A.O. Smith Corporation | Milwaukee | Manufacturing | Tools, Hardware and Light Machinery |
| Sentry Insurance | Stevens Point | Financial Services | Insurance and Risk Management |
| Rockwell Automation, Inc. | Milwaukee | Manufacturing | Tools, Hardware and Light Machinery |
| Bucyrus International, Inc. | South Milwaukee | Manufacturing | Heavy Machinery |
| Diversey, Inc. | Sturtevant | Manufacturing | Chemicals and Petrochemicals |
| Alliant Energy Corporation | Madison | Energy and Utilities | Gas and Electric Utilities |
| Plexus Corp. | Neenah | Manufacturing | Manufacturing Other |
| Spectrum Brands Holdings, Inc. | Madison | Manufacturing | Tools, Hardware and Light Machinery |
| Kohl's Corporation | Menomonee Falls | Retail | Department Stores |
| Snap-on Tools, Inc. | Kenosha | Manufacturing | Tools, Hardware and Light Machinery |
| Fiserv, Inc. | Brookfield | Software and Internet | Data Analytics, Management and Storage |
| CUNA Mutual Group | Madison | Financial Services | Insurance and Risk Management |
| Oshkosh Corporation | Oshkosh | Manufacturing | Heavy Machinery |
| Modine Manufacturing Company | Racine | Manufacturing | Manufacturing Other |
| Northwestern Mutual Life Insurance Company | Milwaukee | Financial Services | Insurance and Risk Management |
| Joy Global Inc. | Milwaukee | Manufacturing | Heavy Machinery |
| Harley-Davidson, Inc. | Milwaukee | Manufacturing | Automobiles, Boats and Motor Vehicles |
| American Family Insurance | Madison | Financial Services | Insurance and Risk Management |
| Johnson Controls, Inc. | Milwaukee | Manufacturing | Heavy Machinery |
| ManpowerGroup | Milwaukee | Business Services | HR and Recruiting Services |
training details locations, tags and why hsg
The Hartmann Software Group understands these issues and addresses them and others during any training engagement. Although no IT educational institution can guarantee career or application development success, HSG can get you closer to your goals at a far faster rate than self paced learning and, arguably, than the competition. Here are the reasons why we are so successful at teaching:
- Learn from the experts.
- We have provided software development and other IT related training to many major corporations in Wisconsin since 2002.
- Our educators have years of consulting and training experience; moreover, we require each trainer to have cross-discipline expertise i.e. be Java and .NET experts so that you get a broad understanding of how industry wide experts work and think.
- Discover tips and tricks about Business Analysis programming
- Get your questions answered by easy to follow, organized Business Analysis experts
- Get up to speed with vital Business Analysis programming tools
- Save on travel expenses by learning right from your desk or home office. Enroll in an online instructor led class. Nearly all of our classes are offered in this way.
- Prepare to hit the ground running for a new job or a new position
- See the big picture and have the instructor fill in the gaps
- We teach with sophisticated learning tools and provide excellent supporting course material
- Books and course material are provided in advance
- Get a book of your choice from the HSG Store as a gift from us when you register for a class
- Gain a lot of practical skills in a short amount of time
- We teach what we know…software
- We care…














