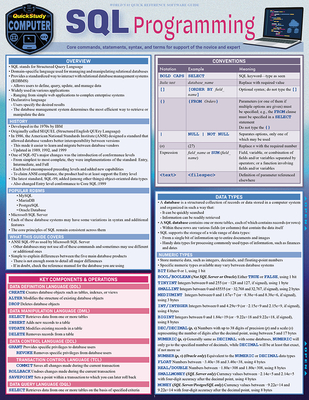
SharePoint Training Classes in Gulfport, Mississippi
Learn SharePoint in Gulfport, Mississippi and surrounding areas via our hands-on, expert led courses. All of our classes either are offered on an onsite, online or public instructor led basis. Here is a list of our current SharePoint related training offerings in Gulfport, Mississippi: SharePoint Training
SharePoint Training Catalog
Course Directory [training on all levels]
- .NET Classes
- Agile/Scrum Classes
- AI Classes
- Ajax Classes
- Android and iPhone Programming Classes
- Azure Classes
- Blaze Advisor Classes
- C Programming Classes
- C# Programming Classes
- C++ Programming Classes
- Cisco Classes
- Cloud Classes
- CompTIA Classes
- Crystal Reports Classes
- Data Classes
- Design Patterns Classes
- DevOps Classes
- Foundations of Web Design & Web Authoring Classes
- Git, Jira, Wicket, Gradle, Tableau Classes
- IBM Classes
- Java Programming Classes
- JBoss Administration Classes
- JUnit, TDD, CPTC, Web Penetration Classes
- Linux Unix Classes
- Machine Learning Classes
- Microsoft Classes
- Microsoft Development Classes
- Microsoft SQL Server Classes
- Microsoft Team Foundation Server Classes
- Microsoft Windows Server Classes
- Oracle, MySQL, Cassandra, Hadoop Database Classes
- Perl Programming Classes
- Python Programming Classes
- Ruby Programming Classes
- SAS Classes
- Security Classes
- SharePoint Classes
- SOA Classes
- Tcl, Awk, Bash, Shell Classes
- UML Classes
- VMWare Classes
- Web Development Classes
- Web Services Classes
- Weblogic Administration Classes
- XML Classes
- RED HAT ENTERPRISE LINUX SYSTEMS ADMIN I
18 May, 2026 - 22 May, 2026 - Docker
27 May, 2026 - 29 May, 2026 - ASP.NET Core MVC, Rev. 8.0
4 February, 2026 - 5 February, 2026 - RED HAT ENTERPRISE LINUX AUTOMATION WITH ANSIBLE
2 February, 2026 - 5 February, 2026 - KUBERNETES ADMINISTRATION
23 February, 2026 - 25 February, 2026 - See our complete public course listing
Blog Entries publications that: entertain, make you think, offer insight
 In May 2012 Google Chrome hit a milestone. It kicked Microsoft's Internet Explorer into excess phone oh that oh that second place as the most used browser on planet Earth.
In May 2012 Google Chrome hit a milestone. It kicked Microsoft's Internet Explorer into excess phone oh that oh that second place as the most used browser on planet Earth.
With Microsoft being in second place, it makes a dark hole for Firefox coming in at number three. Google likes to trumpet three key reasons: security, simplicity and speed.
Available for free on Android, Linux, Mac, and Windows. It gets its speed from the open source JavaScript engine written in C++ known as V8.
In my daily use I use Microsoft's Internet Explorer version 10, Apple's Safari (on OS X) and chrome on both Windows 8 and OS X.
Admittedly people do not know anything about Internet Explorer version 10 since you can only get it on Windows 8/RT.
I do not need a crystal ball to know that the Mother of All Browser Battles is set to begin in the fall of 2012 and beyond.
I have said this before and I'm going to say it again.
What is computer crime? Computer crime, often called “cyber crime” is any type of illegal activity that takes place on a computer with a network. Oftentimes, when you think of computer crime, you might picture a home user downloading a virus that wipes out his hard drive or spyware that hijacks her system for the purposes of spying.
Computer crimes can also affect businesses too and they do, sometimes with devastating results. For example, in 2012, the IRS paid a whopping 5.2 billion dollars in tax refunds to identity thieves!
Protect your business and improve your bottom line by staying one step ahead of the cybercriminals.
5 Common Computer Crimes
As the cloud buzz is getting louder with every passing day you are tempted to take the big leap into the cloud but may have restrained yourself paranoid by ad infinitum cloud security discussions floating on the web. No one can deny the fact that your data is the lifeblood your business. So, undoubtedly its security is of paramount importance for survival of your business. As cloud computing is a paradigm shift from the traditional ways of using computing resources, you must understand its practical security aspects.

Is Cloud Computing Safe?
There can’t be a binary answer (Yes or No) to this question. But with my experience and as an authority on the subject I can tell you that technologies enabling Cloud services are not in any way less secure than the traditional or on-premise hosting model. Also, with the evolution of technology, the cloud providers are getting matured and almost all the providers are offering built-in security, privacy, data backups and risk management as a part of their core service.If you are not a big IT company then you must ask yourself:
· Can an on-premise solution or a traditional hosting provider match the same level of standard security and privacy requirement as provided by the specialist cloud provider whose core competency lies in providing state of the art security and privacy?
Tech Life in Mississippi
training details locations, tags and why hsg
The Hartmann Software Group understands these issues and addresses them and others during any training engagement. Although no IT educational institution can guarantee career or application development success, HSG can get you closer to your goals at a far faster rate than self paced learning and, arguably, than the competition. Here are the reasons why we are so successful at teaching:
- Learn from the experts.
- We have provided software development and other IT related training to many major corporations in Mississippi since 2002.
- Our educators have years of consulting and training experience; moreover, we require each trainer to have cross-discipline expertise i.e. be Java and .NET experts so that you get a broad understanding of how industry wide experts work and think.
- Discover tips and tricks about SharePoint programming
- Get your questions answered by easy to follow, organized SharePoint experts
- Get up to speed with vital SharePoint programming tools
- Save on travel expenses by learning right from your desk or home office. Enroll in an online instructor led class. Nearly all of our classes are offered in this way.
- Prepare to hit the ground running for a new job or a new position
- See the big picture and have the instructor fill in the gaps
- We teach with sophisticated learning tools and provide excellent supporting course material
- Books and course material are provided in advance
- Get a book of your choice from the HSG Store as a gift from us when you register for a class
- Gain a lot of practical skills in a short amount of time
- We teach what we know…software
- We care…